Configure EDGE-to-EDGE encryption
This page provides an example for the configuration of the EDGE-to-EDGE encryption in a site-to-site VPN use case.
Consider the following example:
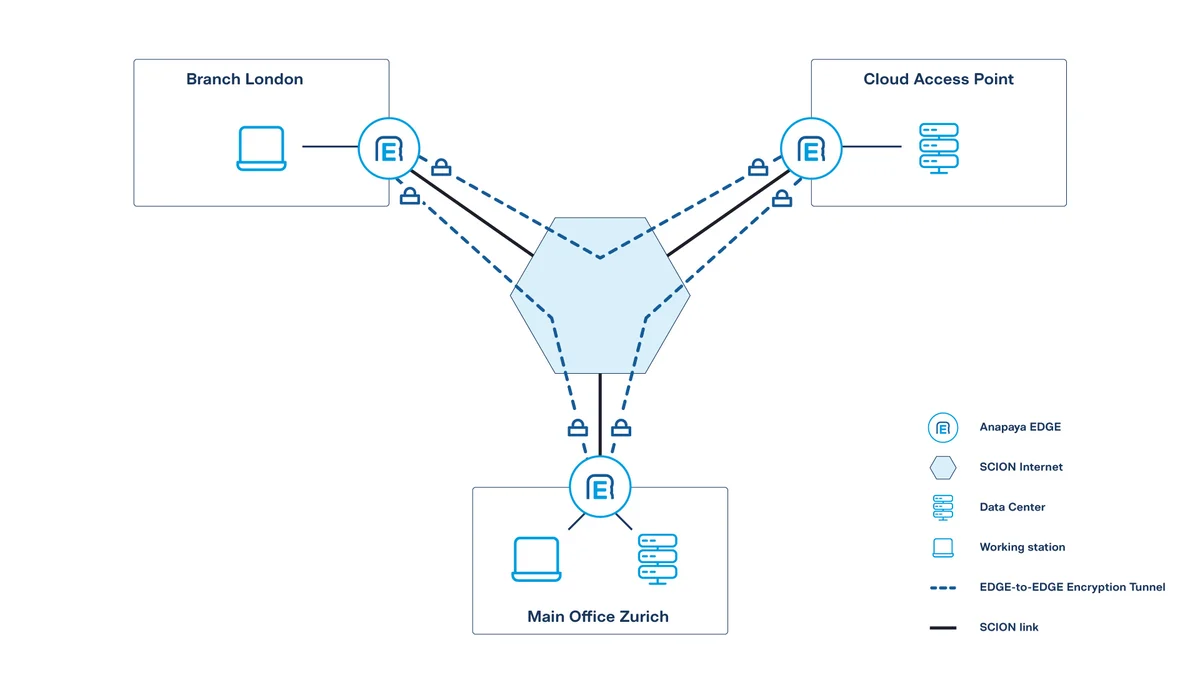
-
Enable the EDGE-to-EDGE encryption feature globally:
{
"scion_tunneling": {
"endpoint": {
"encryption": {
"enabled": true
}
}
}
} -
Configure an IP-in-SCION tunneling domain that encompasses the main office, branch office, and cloud service:
{
"scion_tunneling": {
"domains": [
{
"name": "corporate_network",
"prefixes": {
"accept_filter": [
{
"sequence_id": 1,
"prefixes": [
"192.168.10.0/24",
"192.168.20.0/24",
"192.168.30.0/24"
],
"action": "ACCEPT"
},
],
"announce_filter": [
{
"sequence_id": 1,
"prefixes": [
"192.168.10.0/24",
"192.168.20.0/24",
"192.168.30.0/24"
],
"action": "ACCEPT"
},
]
},
"remote_isd_ases": [
// configure the remote ISD-ASes that correspond to the corporate sites
],
"traffic_policies": [
// configure the desired policies
],
"encryption": "ENABLED" // Enforce encryption for this domain
}
]
}
} -
Apply the domain configurations to the EDGE appliances at the main office, branch office, and cloud service. You will potentially need to adjust the configuration depending on the specific network setup and requirements.
-
Verify the encryption status and connectivity between the sites using the Anapaya Console or CLI. You can check the status of the tunnels and the encryption status for each domain:
$ appliance-cli info tunneling
Endpoint:
Status: ✅
Domains:
- Name: corporate_network
Status: passing ✅
Encryption: enabled
Prefixes Received: 2
Prefixes Announced: 1
...